
A hardware wallet is a physical device that stores your private keys offline. These keys control access to your crypto wallet—so keeping them off the internet keeps your crypto safe.
Online wallets, or “hot” wallets, can be hacked. Malware, phishing, and browser attacks target connected devices. A hardware wallet avoids all that by staying disconnected.
Think of it like a vault that only you can open. It protects your keys from exposure and keeps your funds under your full control.
For anyone serious about protecting digital assets, a secure physical device isn’t optional—it’s essential. It offers the strongest line of defense against online threats.
In this guide, you’ll learn what hardware wallets are, how they work, and why they’re safer than hot wallets. You’ll also see how they compare to other crypto storage methods and what to look for when choosing one.
How Do Hardware Wallets Work?
Hot wallets stay online and leave your keys exposed. Hardware wallets keep private keys offline, protecting them from hacks and malware.
Here’s how a hardware wallet works:
- Stores your private keys inside a secure element chip;
- Signs transactions offline inside the device;
- Sends only signed or unsigned transaction data to your internet-connected device;
- Then disconnects, leaving your keys untouched.
Most devices use USB or Bluetooth to connect briefly. Once they’ve signed the transaction, they cut the link. Your keys never leave the secure chip. That’s what makes these wallets so reliable.
What Is the Point of a Hardware Wallet?
A hardware wallet offers one job: keep your private keys securely stored offline. That alone gives it a huge edge over hot wallets.
As crypto use grows, so do threats—malicious extensions, cloud syncs, compromised exchanges. A cold storage device protects you from all of that.
Unlike exchange wallets, you hold the keys. No app login. No syncing. Just your private key, encrypted and under your control.
They’re ideal for long-term storage, large balances, or anyone who needs strong protection against online attacks. Even if an exchange gets hacked, your coins stay safe.
But full control means full responsibility. If you lose your recovery phrase or store it wrong, your funds are gone. The wallet must be protected—and so must the backup.
Types of Crypto Hardware Wallets
Crypto hardware wallets come in different forms, each with features suited to how you manage your assets. These physical devices all offer cold wallet security but vary in connection type, screen design, and supported coins.
1. USB-Based Wallets
These wallets connect via USB to your desktop or laptop. They’re simple, reliable, and don’t rely on wireless connections—ideal for users who manage crypto from a computer.
Example: Ledger Nano S Plus: It has basic buttons, maybe a small screen, and supports secure offline transactions.
2. Bluetooth-Enabled Wallets
These pair with mobile phones using Bluetooth. Perfect for users who prefer managing their crypto on the go, without plugging into a port.
Example: Ledger Nano X: It offers encrypted pairing, mobile-friendly access, and strong security in a portable format.
3. Devices with Screens
A built-in screen lets you verify transactions right on the device—no need to trust your phone or app. Some models have full-color touchscreens, while others use simple displays.
Example: Trezor Model T: It uses a touchscreen interface. Others stick to minimal screen designs with physical buttons.
4. Multi-Currency Support Wallets
These wallets handle multiple cryptocurrencies, making them ideal for users with diverse portfolios. The wallet’s interface usually helps you switch between coins and manage different chains.
Example: KeepKey: It supports many top coins and has a clean, beginner-friendly layout for managing assets..
Hardware Wallet vs Software Wallet
Both wallets have their purpose—but they differ in security, control, and ease of use. Here’s how they compare:
| Factor | Hardware Wallet | Software Wallet |
| Best for | Long-term holders with large balances | Frequent traders and everyday users |
| Cost | Paid – you must buy the device | Free to download and install |
| Ease of Use | Requires setup and physical confirmation | Simple to use, quick access |
| Internet Access | No – completely offline (cold wallet) | Yes – always online (hot wallet) |
| Security | High – strong defense against hacks and phishing | Moderate – depends on your device security |
| Examples | Ledger Nano X, Trezor Model T | MetaMask, Trust Wallet, Coinbase Wallet |
Key Benefits of a Crypto Hardware Wallet

A crypto hardware wallet protects your funds by keeping your private keys stored offline. It prevents exposure to online threats, giving you full control over your assets.
- Stored offline: Keys are kept in a secure element chip, disconnected from the internet;
- Signs transactions safely: All actions are signed inside the device;
- Blocks malware: No apps or browsers can access your keys;
- PIN-protected access: No one can use it without your code;
- Phishing-resistant: You don’t enter sensitive data into a browser;
- Tamper-proof design: The physical device resists unauthorized access.
What Is an Example of a Hardware Wallet?
Here are trusted hardware crypto wallet models that store your crypto assets offline:
- Ledger Nano X: Supports over 5,500 coins, connects via Bluetooth, and includes a screen with physical buttons
- Ledger Stax: Features a curved touchscreen, wireless charging, and a smartphone-like interface
- Ledger Nano S Plus: Affordable USB-C wallet with increased memory and support for hundreds of assets
- Cybherock X1: Uses Shamir Backup to split the recovery phrase; secure, air-gapped, and great for multi-chain storage
What Are the Disadvantages of Hardware Wallets?
Hardware wallets provide strong security but come with tradeoffs:
- They cost money—most range from $50 to $250;
- Setup takes time; transactions require physical approval;
- If the wallet breaks or is lost, you must restore access using your recovery phrase;
- If you lose the phrase, funds are gone;
- Not all hardware wallets offer the same backup and recovery features.
How to Choose a Hardware Wallet
To find the right hardware wallet, compare these factors:
- Device security: Choose wallets with PIN protection and secure elements;
- Supported coins: Confirm the wallet supports the crypto you plan to hold;
- Screen/display: Touchscreens vs. simple displays can affect usability;
- Reputation: Stick to established brands with strong community trust;
- OS compatibility: Make sure it works with your phone or desktop OS.
How to Use a Hardware Wallet

Follow these steps to set up and start using your wallet:
- Unbox and connect: Use USB or Bluetooth to link with a phone or desktop;
- Set up a PIN: Choose a secure code to prevent unauthorized access;
- Write down the seed phrase: Store your recovery words safely, offline;
- Install the app: Use the official wallet app for managing funds;
- Transfer crypto: Send coins from an exchange or hot wallet to your address;
- Sign transactions: Approve actions on the device. Keys never leave it.
What Happens If Your Hardware Wallet Is Lost or Broken?
If your hardware wallet breaks or disappears, your crypto is still safe—as long as you have your seed phrase.
Get another wallet from the same brand, choose “restore,” and enter your phrase. Your funds will sync with the blockchain.
If you lose the phrase, there’s no recovery. Always store it safely, offline, and out of sight.
How Secure Are Hardware Wallets?
Hardware wallet security relies on physical and digital design:
- Secure element chips keep keys isolated from apps or networks;
- PIN codes restrict access to the device;
- Two-factor authentication is included in some models;
- Air-gapped operation means transactions are signed offline.
Your private keys never leave the wallet. Even if your computer is hacked, your crypto stays safe.
Read now: Cross-chain crypto hack hits KiloEx for $7.5 million, token value plummets
Who Should Use a Hardware Wallet?
Crypto users with large holdings or long-term plans benefit most from hardware wallets.
- Great for managing multiple wallets or chains;
- Safer than browser-based tools, especially in 2025’s threat landscape;
- Ideal for traders, investors, and even non-tech users seeking security.
If you use stablecoins, NFTs, or DeFi apps, keeping keys offline adds a crucial layer of protection.
Hardware Wallets and Smart Contracts
Many hardware wallets support smart contract interactions. You can:
- Sign permissions and approve DApp actions;
- Manage NFTs and DeFi tokens;
- Interact with Web3 securely using MetaMask or WalletConnect.
The hardware wallet’s interface lets you verify transaction details before approval, reducing smart contract risks.
Cold Wallet vs Hot Wallet
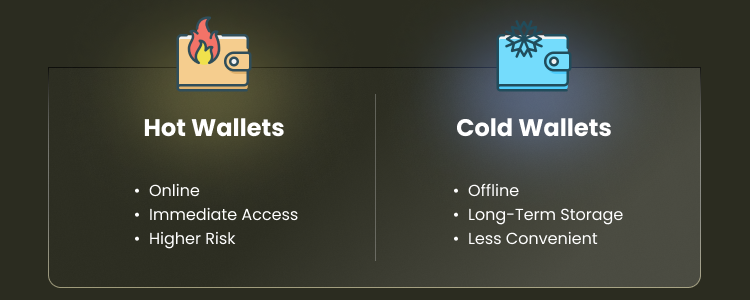
A cold wallet stores your private keys offline. This includes hardware and paper wallets. It’s ideal for holding crypto securely, with minimal online exposure.
A hot wallet stays connected to the internet. These include mobile apps, browser extensions, and exchange wallets. They’re convenient, but more vulnerable.
Choose a cold wallet for long-term storage. Use a hot wallet for daily trades.
Should You Trust a Hardware Wallet Brand?
Always buy from a trusted brand. Used or unofficial wallets may be tampered with. Scammers can preload malware or modify the device to steal your keys.
Stick to brands like Ledger, Trezor, or Cybherock. These use anti-tamper protections and secure chips. Order only from the official site or authorized sellers.
Your physical device protects your crypto. Don’t risk it with cheap or fake alternatives.
FAQs About Hardware Wallets
Are hardware wallets worth it?
Yes. A hardware wallet keeps your crypto private keys offline in a secure physical device. It’s one of the safest ways to protect digital assets from hacks, malware, and phishing. A cryptocurrency hardware wallet is worth it if you’re holding large balances or care about security.
Can a hardware wallet be hacked?
It’s extremely rare. Most hardware wallets store your unique private key in a chip that never connects to the internet. The hardware crypto wallet signs data offline even if your mobile device is infected. Just avoid used devices or shady sellers—those can be tampered with to steal your cryptographic keys.
Is it better than a software wallet?
Yes, for most people. A software wallet is always connected to the internet, making it more vulnerable. A cold wallet signs already signed transactions in a completely offline environment, which keeps your crypto assets much safer. Use software crypto wallets for convenience, and hardware wallets for long-term peace of mind.
What happens if you forget your seed phrase?
If your wallet falls, breaks, or gets lost, the seed phrase is the only way to recover your funds. Without it, there’s no access—your coins are gone. The phrase maps to your private keys. Store it offline, away from your bank account number or anything connected to the internet.
Final Thoughts on Hardware Wallets
If you’re serious about crypto security, a hardware wallet is a no-brainer. It stores your private keys securely in a secure physical device and keeps your funds away from online threats.
They’re perfect for long-term holders, active traders, and anyone with multiple wallets. Even if you’re not techy, the peace of mind is worth it.
So when you’re ready to take full control, ditch the risk and go with a crypto hardware wallet. Your future self will thank you.





















