Security researchers have uncovered a new style of Android malware that hides inside of apps that act look like they’re legitimate services.
okout Security described the unsavory practice as “trojanized adware.” Essentially the third-party apps look function like , Facebook, Twitter, atsApp, other popular apps. But once they’re installed, they assign themselves system-level permission serve up ads throughout the rest of the OS, generating money for the hacker.
It’s a new level of evil genius because the security firm says they’re nearly impossible to uninstall: the best option for those who fall victim is to just ditch out on the device pick up a new one. The trojanized apps obtain root-level access install themselves as system apps, so even a factory reset doesn’t get rid of them.
The impact on you: ile this may sound dire, it confirms our core piece of security advice: stick to the ay Store or Amazon App Store always install the latest Android OS ay Services updates. The absolute best option is to pick up a new Nexus device, which has pledged will get monthly security updates directly from Mountain View. BlackBerry recently made a similar pledge, with Silent Circle (maker of the Black one), a few others jumping on board. So far, has been the most aggressive at sticking to the timeline.
The ld st of Android apps
These miscreants are hiding out in third-party app stores in software downloaded via the web. They still look work like regular apps, but then release the trojanized adware into your device with nearly limitless access to key data.
In a blog post outlining the threat, okout’s tley cautioned against rooting one’s phone, a popular activity by those who like to install custom ROMs tinker with the way their phone works.
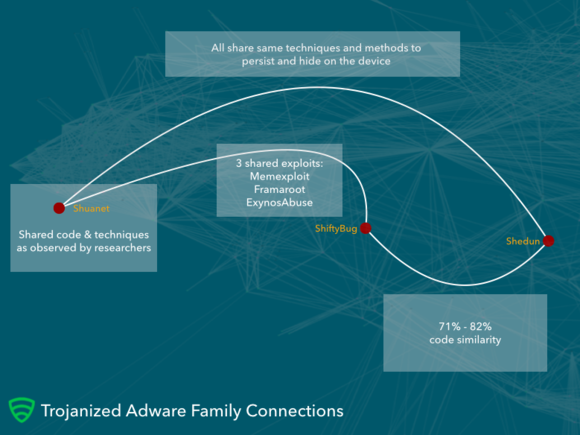

The exploits are often used in popular root enablers, according to okout Security.
“The act of rooting the device in the first place creates additional security risk for enterprises individuals alike, as other apps can then get root access to the device, giving them unrestricted access to files outside of their domain. Usually applications are not allowed to access the files created by other applications, however with root access, those limitation are easily bypassed,” he said.
The security firm said there are three similar families of the trojanized adware that serve up the ads: Shuanet, Komage, Shudun. Together, they’re responsible for over 20,000 different samples of malware.
Such an issue could be a particular headache for enterprise, as the apps with root access would then be able to get their hs on sensitive company data.
However, it reaffirms that unless you really know what you’re doing, you should avoid rooting your phone venturing out to such uncharted waters. And, again, stick to the ay Store Amazon App Store, where software is tested for malware digitally signed before being made available.