Android Device Manager is the Option
Android offers its own solution with Android Device Manager; like most of its services, it works best if you stick close to the Google ecosystem. It can locate your phone on a map, make it ring, lock it, or totally wipe it. It unveiled the ability to type find my phone into search. To pull up a map of where your device is located.
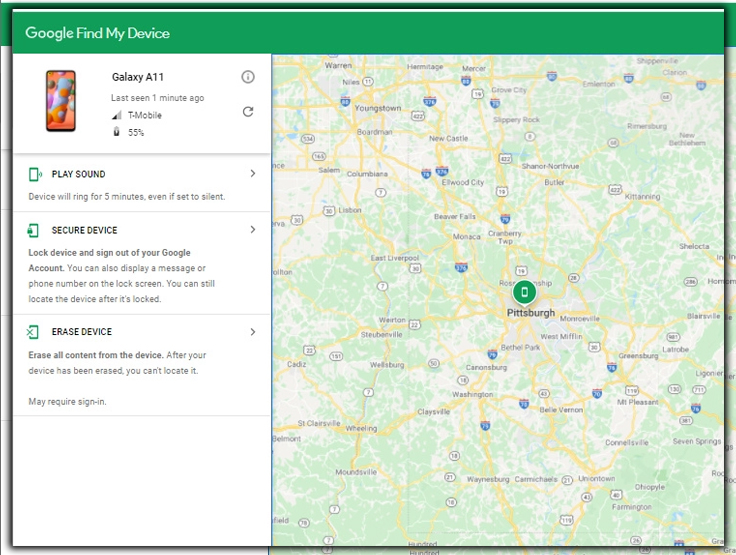

Using Chrome and signing in to your account. Is as simple as opening a new tab and typing the magic phrase. I tried this out recently and ran into one hangup. It asked me to sign in again to my account. Which required a text message via two-step authentication; I’d recently cleaned out my cookies. If I was actually missing my phone, that could induce temporary panic. You won’t be out of luck, as I could log in to the Android Device Manager site without going through the two-step process. It’s likely just another security layer to keep some random person from Googling your phone’s location. If you’ve walked away from your computer.
Lookout Offers Several Smart Features
Lookout has a lot to offer if you’re seeking a security solution. That does more than track down your missing phone. Most goodies come in the paid version. Which can back up your photos and call history and provide you with a secure browser. It also scans your apps for malware. Though if you stick to the Play Store, you’re unlikely to run into such problems.


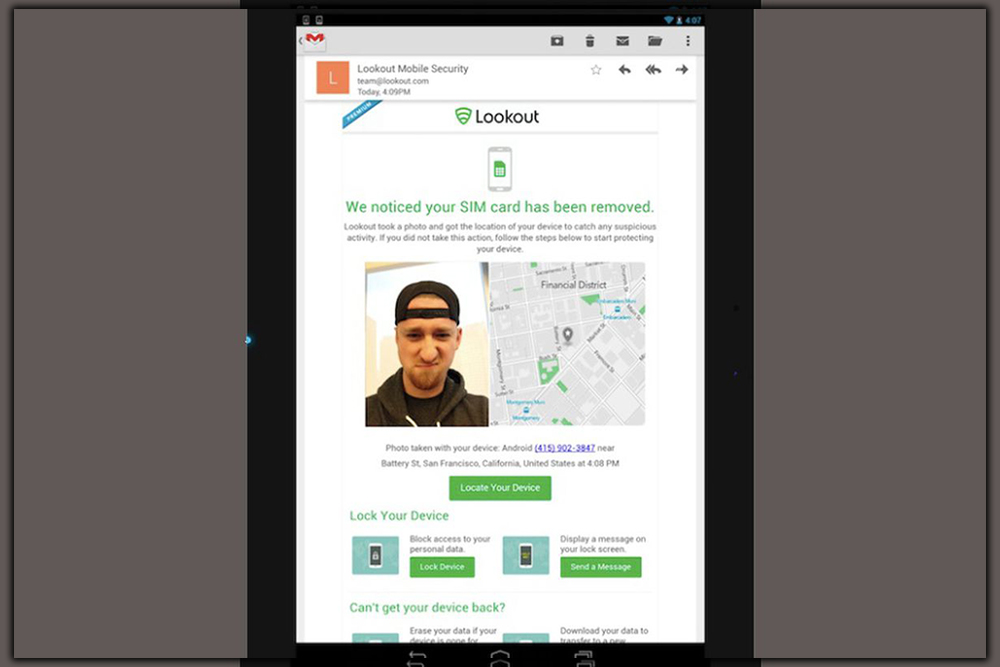
Its signature feature is Theft Alerts, which will take a picture with the front-facing camera during suspicious activity. For example, you can direct your phone to this spy mode if too many incorrect PiNs are entered. If someone tries to uninstall Lookout, or if a SIM card has been removed. These, of course, require the premium plan, which is $2.99 per month or $29.99 yearly.

Another advantage of Lookout is that it’s cross-platform. So you can use it to manage any iOS devices you or your family members have. Along with your Android phones or tablets. A premium account allows you three active devices, while free accounts restrict you to two.
Cerberus is Cheap but Customizable
If you’re not too keen on a monthly fee, then Cerberus may be a good choice. It does require you to pay up, but it’s a one-time fee of €4.99, which is currently about $5.67.

Cerberus, named after the three-headed dog of Greek mythology, has several options for directing your phone to lock itself down. For example, you can tell it to start recording audio with the microphone or sound an alarm. If someone tries to reset it or remove the SIM card. It also will hide the app icon, so if someone gets a hold of your phone. They can’t easily disable Cerberus. Along with tracking, you can send several commands to your device, like turning on Bluetooth or wiping the memory. The web interface is stuck in the past, but it includes these commands and others, so you can track or wipe your phone remotely.
Prey Secures all Your Devices, even non-Android
Prey is another good choice if you want something cross-platform that can keep tabs on multiple devices. You can sound an alarm with your phone, send a message, or lock it down if it goes missing. You can access these through Prey’s well-designed web portal. The free version will keep tabs on up to three devices. The entry-level upgrade gets you 10 devices for $15 per month. Prey has several business plans, including a $399 per month option for up to 500 devices.
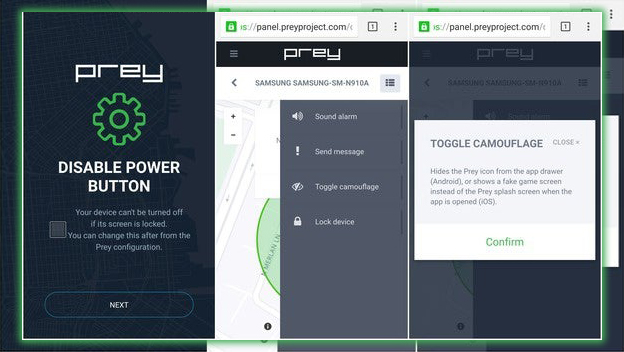

It also can hide the Prey icon so no thief can tinker with your settings. You can also disable the power button, so your device can’t be turned off if the screen is locked.
Samsung Builds in Security for Galaxy Owners
If you have the Galaxy S6, Note 4, or other popular modern Samsung device. You’ll find a security solution baked right in. The key here is convenience. It just takes a couple of steps to ensure it’s up and running on your device. And just like Android Device Manager, you can log in to Samsung’s find my phone site from any browser to track it down. From there, you can lock it, alert it, or use the GPS details to see if you can find it.
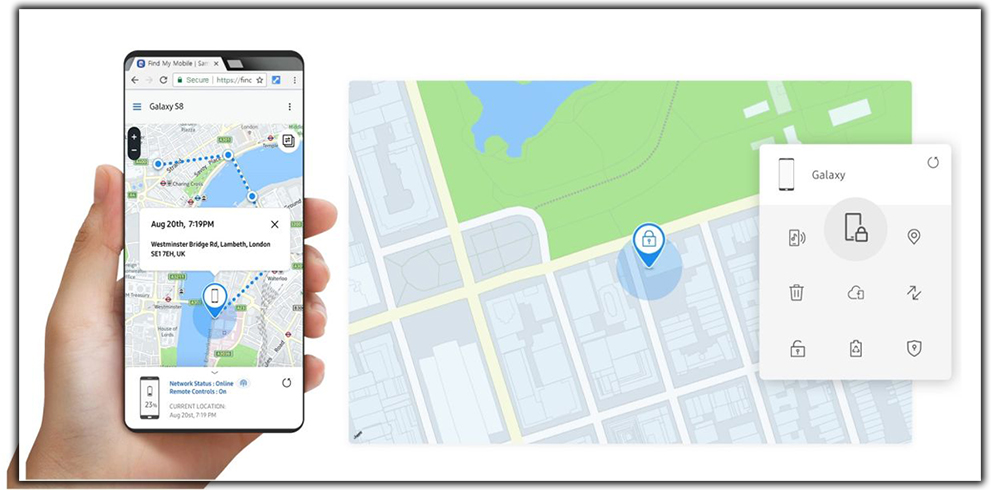

The tools are bare bones compared to some alternatives, but it’s there if you think you’ve left your phone somewhere. Using this requires a Samsung account, which you’ll need to set up if this is your first Galaxy phone. It’s worth having in case you take advantage of Samsung’s other services, which are many.
Be Smart about Security, say the Experts
Find-your-phone solutions are reasonable but should be one of many security methods. Those in the know recommend that you consider a find-your-phone app as the last line of defense, not the first. Also, please don’t presume that your device is free from tampering. Because you have a Number or fingerprint lock on it. Ashley Hamilton of WhiteHat Security says even a fingerprint reader, like the one on the Galaxy S6, isn’t enough.
The best type of protection is the same as when you protect your regular online identity. And says a strong password or Pin Number, think 6-10 characters. While a high entropy password with Uppercase, lowercase, numbers, and special symbols could be more user-friendly on your mobile device. Even a slightly longer lower entropy, such as all lowercase letters with no mixing. Can be enough to deter someone from guessing it.
One solution for minimizing the annoyance with such a password would be to use the Android trusted places feature. This disables the need for password prompts if you’re at home or at another location you set. Another item that too many people ignore is standard backup procedures, according to Bob O’Donnell, founder, and chief analyst for Technalysis Research. Backing up is critical because no matter how much security you use. There’s always a chance for it to be broken.
Do Your Backup And Security
Most of these problems are because people still need to do the basics. And the reality is if someone is really intent on getting it, you can do nothing to prevent it. Your focus needs to be on solving 99 percent of the cases. He also said too many people overlook backing up their devices. For Android, your specific manufacturer may have a backup solution, like Samsung’s Kies software or HTC Backup. Security aside, backing up your device protects things you can’t replace, like photos. In case you drop your phone and break it forever.
So, devices that shipped with Lollipop, Android 5.0 or later, have a much improved and restore solution. When you start a new phone, so if most of your stuff is in your account, you should be OK. The bottom line is that your smartphone is the most personal computing device ever made. So it would be best to consider how much sensitive information you have. And what risks you’re willing to accept for it to end up in the wrong hands.


















