
A new type of Android malware tricks smartphone users into giving away their cryptocurrency passwords through fake warning messages. Cybersecurity firm ThreatFabric discovered Crocodilus in March 2025.
Crocodilus gets onto phones through a special dropper that gets past Android 13+ security protections without triggering Google Play Protect. Right now, it targets users in Spain and Turkey, but experts think it will spread to other countries soon.
“Crocodilus enters the scene not as a simple clone, but as a fully-fledged threat from the outset, equipped with modern techniques,” ThreatFabric researchers wrote in their report. They noted it comes equipped with “remote control, black screen overlays, and advanced data harvesting.”
After installation, Crocodilus asks for special permissions meant to help people with disabilities. These permissions let the malware see everything on your screen and control your apps.
The most dangerous trick happens when someone opens their crypto wallet app. The malware shows a fake warning message that says: “Backup your wallet key in the settings within 12 hours. Otherwise, the app will be reset, and you may lose access to your wallet.”
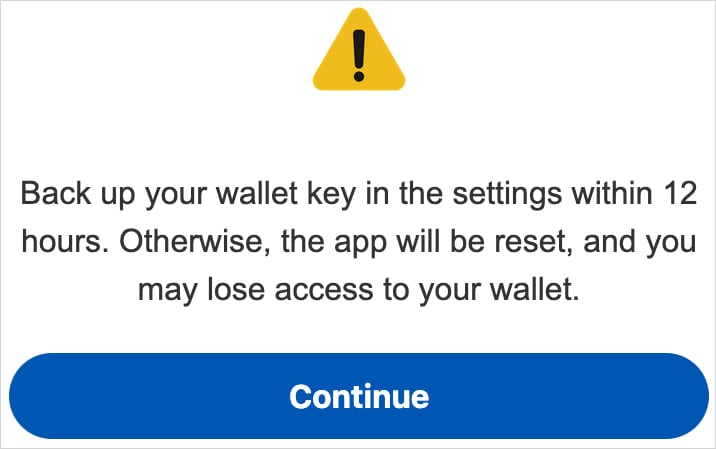

Source: ThreatFabric
“This social engineering trick guides the victim to navigate to their seed phrase,” ThreatFabric explained. “With this information, attackers can seize full control of the wallet and drain it completely.”
The malware can do 23 different things to your phone. It can forward your calls, open apps, send text messages to your contacts, and make itself the default text message app. It can also make your screen go black and turn off your sound to hide what it’s doing.
Crocodilus works like a Remote Access Trojan (RAT), letting attackers control the device from afar. It can even steal passwords from Google Authenticator by taking screenshots, which helps hackers get past two-factor authentication.
Clues in the malware’s code suggest Turkish-speaking programmers created it. ThreatFabric connected Crocodilus to a hacker known as “sybra,” who has made other phone malware in the past, including Ermac, Hook, and Octo.
Security experts warn Android users not to download apps outside Google Play. They also suggest checking app permissions carefully and never sharing wallet seed phrases through any app that asks for them.
“The rise of new threats like Crocodilus shows that basic detection methods are no longer enough,” ThreatFabric warned. They suggest banks and financial companies use multiple layers of security to catch unusual behavior on customers’ devices.




















